Archaeology
A Tool For Digging Into Binary Files on macOS
Binary Files Are Everywhere in macOS
macOS uses many different binary file formats.
![]() Some — like binary property lists — have broad tool support and are relatively easy to inspect...
Some — like binary property lists — have broad tool support and are relatively easy to inspect...
![]() Some — like X.509 certificates, configuration and provisioning profiles
or App Store receipts — use standard formats, but lack macOS-native inspection tools, or
only have command-line tools that can be awkward to use...
Some — like X.509 certificates, configuration and provisioning profiles
or App Store receipts — use standard formats, but lack macOS-native inspection tools, or
only have command-line tools that can be awkward to use...
![]() Some — like compiled nibs, keyed archives, code signatures or URL bookmarks — use Apple-proprietary formats
that are not documented and that have no (public) inspection tools.
Some — like compiled nibs, keyed archives, code signatures or URL bookmarks — use Apple-proprietary formats
that are not documented and that have no (public) inspection tools.
Even a file in a well-known format often contains data blobs encoded in one of the other formats — such as an app's preferences property list, which might contain URL bookmarks or an archive of serialized objects.
Archaeology Can Help You Inspect (Some of) Them
Archaeology gives you a way to dig into a number of these binary files.
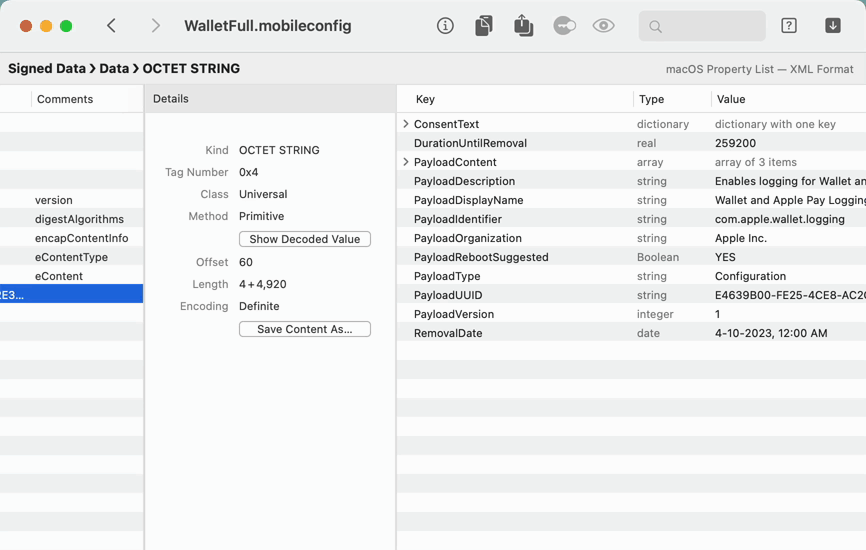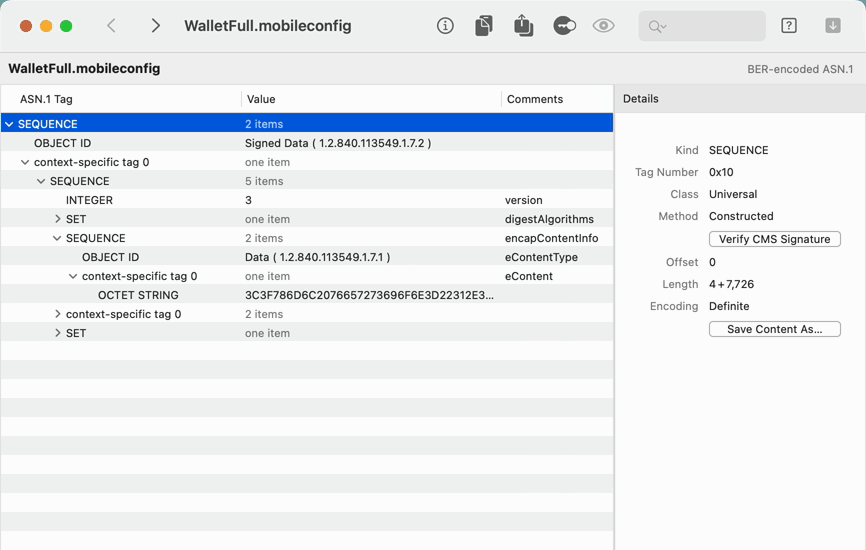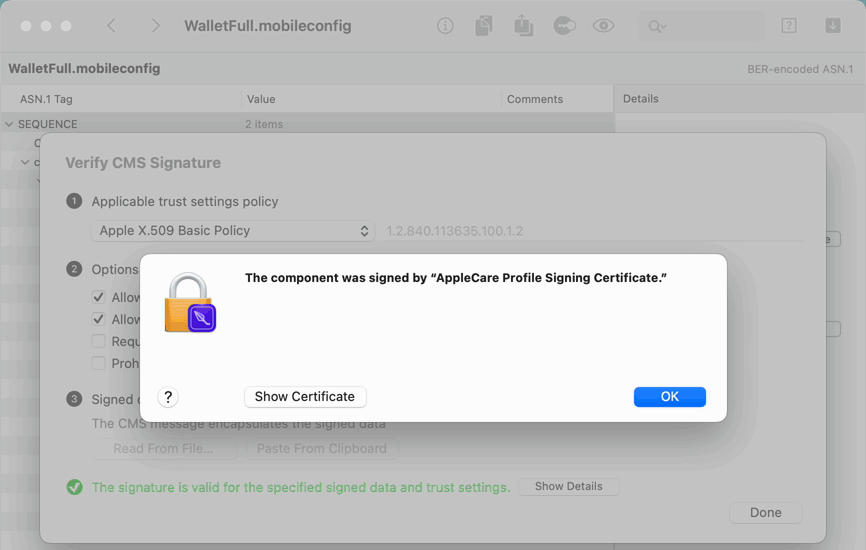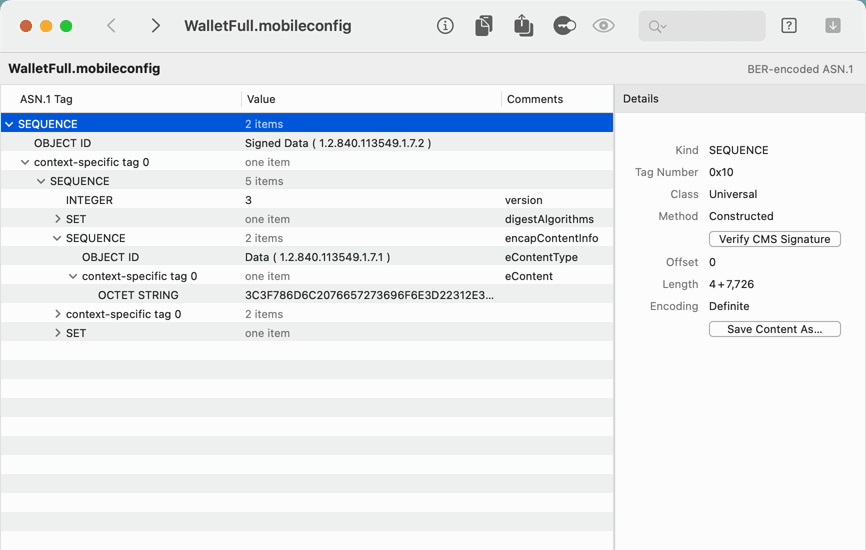
- For example, open a configuration profile — which is BER-encoded ASN.1
- Find and decode the “payload,” which is a macOS property list
- Even verify the signature on the CMS, and inspect the certificate that created it
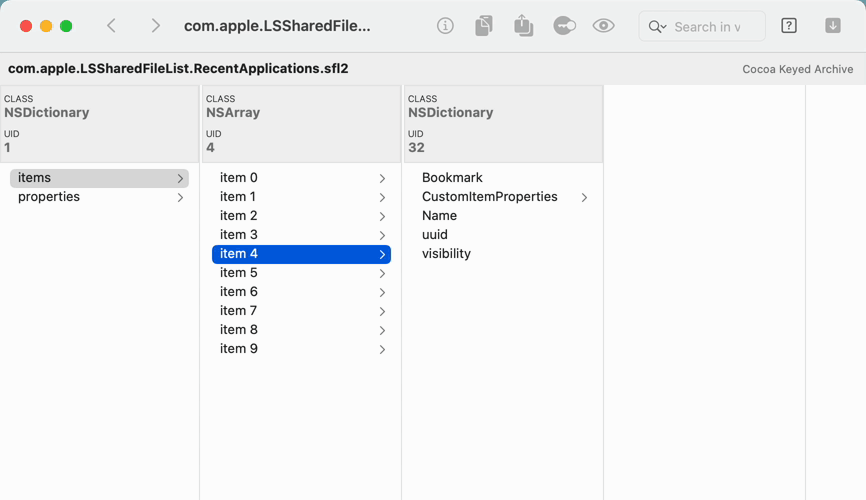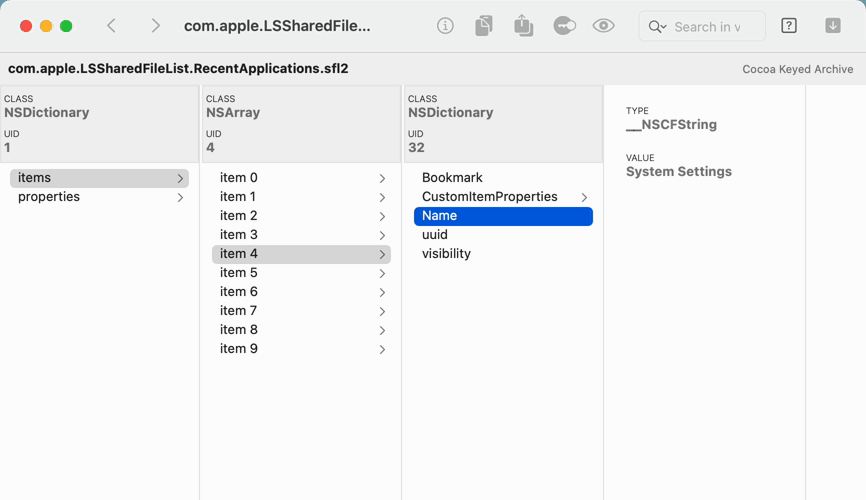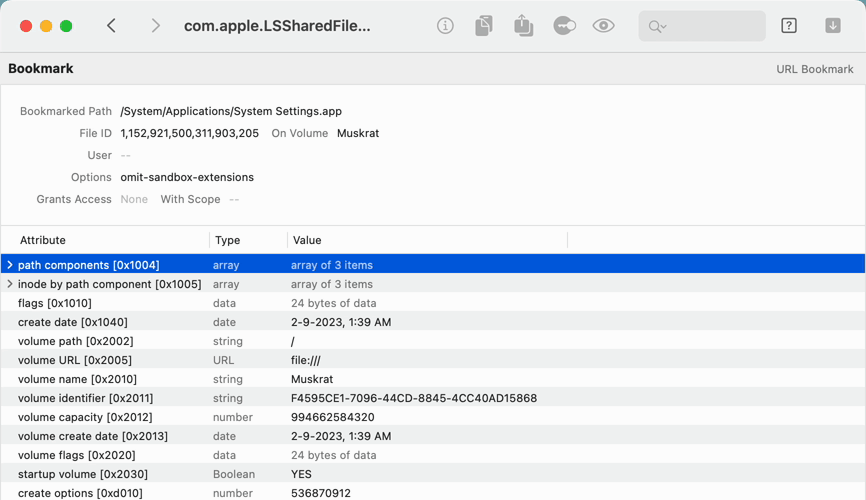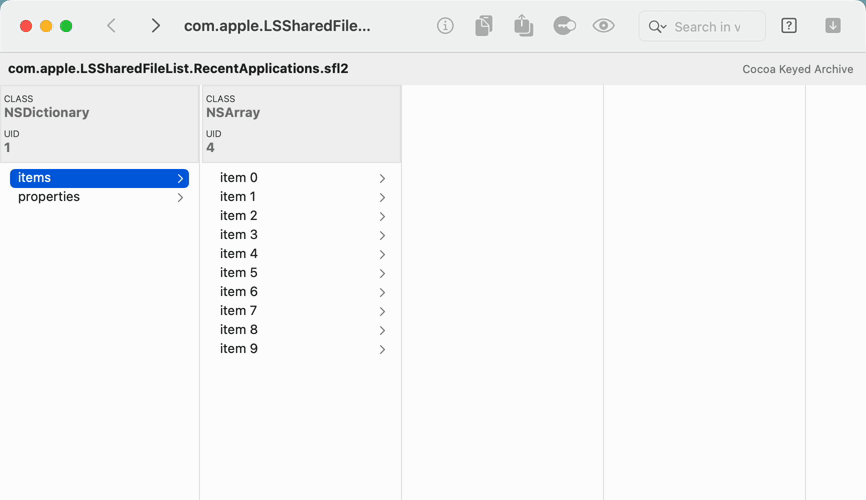
- Or, open the macOS file that stores your “Recent Applications,” which is a Cocoa Keyed Archive
- Trace the object graph in the
sharedfilelistdmodel, and see the applications in this list - Find and decode an application's URL Bookmark
That's just a couple examples — see Formats for all of the different types of binary formats that Archaeology can inspect.
Wait, why do I want this?
We'll be the first to admit: Archaeology is a very niche tool — even by the standards of our already-niche products!
We originally built Archaeology for ourselves — just for debugging our products, and for debugging day-to-day problems we encounter with macOS. We hadn't really intended to release it. But then we kept finding it ... useful. Again and again. So we finally decided that maybe someone else could also get some use out of it.
But if you don't see why you'd want this, the chances are that you probably don't?